The Mystery of the IP 192.168.1.18
Hello Network! Today I wanna tell a story... A story that happened at 2:32 in the morning while I was studying on #TryHackMe about Endpoint Security as part of my SOC Level 1 path. In that room I got introduced to TCPView and Process Explorer, 2 Microsoft official tools that you can download from here:
Disclaimer
Everything Im going to show here is for educational and entertainment purpose. Never make this steps on a network that you are not allowed to do it or you dont own. Performing any CyberSecurity audit on a network that you don't have permission to do it can inflict legal consecuences. Go safe, be ethical and enjoy.
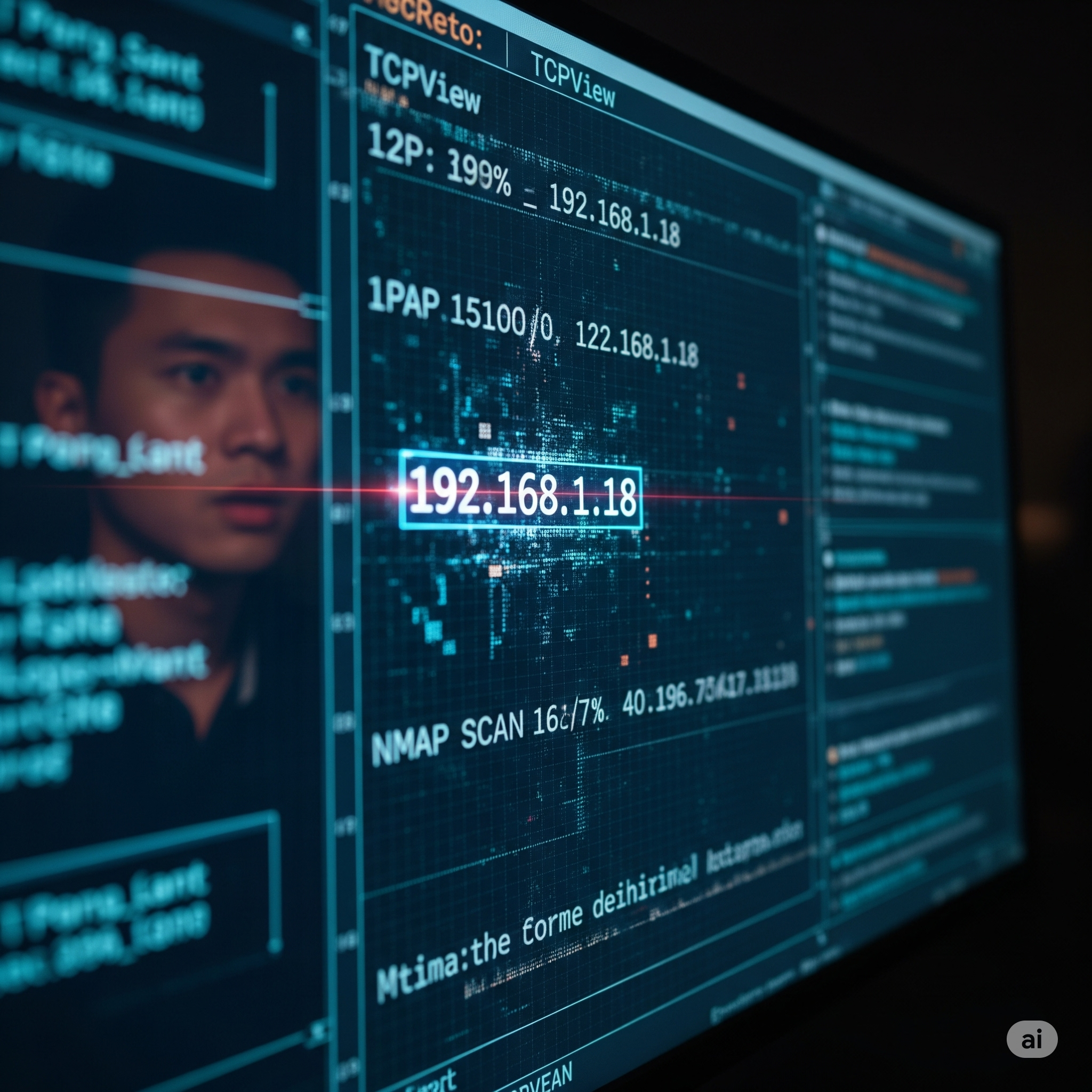
Anyway, I was thinking this part of the path was too theorical and I wanted to put my hands on real analytic scenario. So I decided to run a port scan with nmap on my local network (always do this kind of stuff in your local environment or with authorization!), after the scan finished I found something weird on TCPView. One IP appeared: 192.168.1.18
At first, I wasnt sure why that IP appeared but something bothered me a lot: That IP keep conections open on TCPView. I was 100% sure that wasnt my private IP or any private IP on my local network since I know the IPs of my home network... so I thought:
Somebody is connected to my network!
The adrenaline rushed, the nervious started to appear and shivers on my spine raised like I was found gold, oil, or something even better: Houses on a cheap price!
Needed to dig more about this IP.
First, I ran a new nmap but specifically on that IP through all ports to figure out what ports had open and which service was running on them:
nmap -p- -sCV 192.168.1.18 --open -vvv
Lets explain a bit what this command means:
- •
nmap: A tool used to discover hosts and services on a network. A key part on the offensive recognition (Red Team) or monitoring and auditory (Blue Team). - •
-p-: Scan all the ports from 1 to 65535. By default, nmap scans only the firsts 1000 common ports, using-p-, we are telling nmap to run though all the possible ports, even the not standars. This is usefull because a lot of malware settings or services hiddes the communication in more higher ports, for example: Redis sometimes runs on 6380, hidden panels on 8081, 5000, 49152, etc. - •
-sCV: This is a combination of 2 technical options:- •
-sC: Actives the default detection scripts from nmap (NSE Default category). Uses a collection of NSE Scripts for gathering information from the services like: Banner, OS Info, Anonymous Users on SMB, supported protocols, bad configurations, etc. - •
-sV: Service/Version detection. Try to determinate what service is running on each open port and what is the exact version of that service.
- •
- •
192.168.1.18: The misterious IP I found on TCPView... - •
--open: This flag filter the output to only show the opened ports, not showing the ports are closed or filtered (Filtered means that the ports might exist and be open but nmap cannot reach to it, maybe because is behind of a firewall). - •
-vvv: nmap have different output detail level:- •
-v: verbose (level 1) - •
-vv: more detail on the output - •
-vvv: even more detail on the output before activate-d(debug mode).
- •
After the scan, I found a lot of services such as Redis, PostgreSQL, MySQL, SMB and MSRPC. Yes, I agree, I have those services on my host/personal machine (at the end, even if Im moving to a more CyberSecurity role, im still a fullstack developer) but that IP still bothered me, because it wasnt my personal host IP machine.
I decide to deep dive more into it, I thougt: "Maybe my machine was pwned? how? I never download anything suspicius on this machine... maybe I went pwned thought one of my VM?"
Run again nmap but now more targetted and with the vuln script and I found the redis have full access without any password...
I tried to connect to the redis server through:
redis-cli -h 192.168.1.18
and confirm, that server dont have any password or authentication method setted up. Ran INFO into the redis server to see if there is any info on it. Nothing...
Research in depth
Come back again to TCPView and I saw that every time I ran the nmap script, a connection was ESTABLISHED to that IP but when I ran the script:
arp -a
The IP dont exist... no MAC address, no IP connection, no trace, nothing... That shoot my paranoia to the sky: "Maybe I have a zombie machine on my network? or there is an uknown device connected, now for real?" That IP response with the same services I got in my personal/host machine, but that IP dont exist on any of the scans I made it. Im on Windows 11 at the moment, usually I use Linux on my personal machine so after a lot of research and digging into my notes I found a Windows command:
Get-NetIPAddress -AddressFamily IPv4
This cmdlet gets the IP address configuration, such as IPv4 addresses, IPv6 addresses and the IP Interfaces with which addresses are associated on a windows machine. (Official documentation of this cmdlet here).
Found it!... the IP 192.168.1.18 was there. Appeared as "deprecated" but was there.
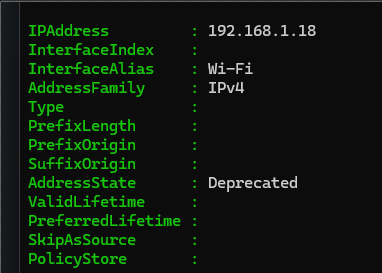
The IP was associated to the WI-FI interface and I remembered that my motherboard have 2 ways to be connected: Ethernet and WI-FI.
A couple of months ago, I used the WI-FI on my host machine (connected the anthenas to the motherboard) because I had my Ethernet cable a bit doomed. Windows 11 in that moment, saved the interface and that Private IP was assigned to it but since I re-connected my PC to a Ethernet cable again, marked this Interface as deprecated, thats why it wasnt showed when I ran: ipconfig, arp -a or any of the net utils scripts that Windows gave it to us out of the box but appeared on nmap scan and TCPView.
I was scanning my own PC... I was the intruder, the analyst and the hacker.
Not gonna lie, I felt a bit dissapointed BUT... I learn a lot about false positives, about TCPView, that Windows is more interesting (at powershell level I mean) that I thought and one important lession:
Next time that you saw something weird on your network, be sure that you are not scanning yourself 😂😅